Identity Management for Unix allows you do to things like authenticate against Active Directory from a *nix system using LDAP or other tools. Refer to this technet article for full instructions on installing the components; the synopsis is below. Afterwards you will need to set up some user and group attributes.
WARNING: It appears that Identity Management for UNIX has been removed in Server 2012 R2. While there are workarounds, they involve editing your Active Directory schema directly (which is dangerous) and are beyond the scope of this article.
In Server 2008/R2 do the following:
To install Identity Management for UNIX components
- Open Server Manager. To open Server Manager, click Start , point to Administrative Tools , and then click Server Manager .
- In the tree pane, expand Roles .
- On the role home page for AD DS, in the Roles section, in the list of common tasks, click Add Role Services .
- On the Select Role Services page of the Add Role Services Wizard, select the Identity Management for UNIX role services that you want to install, and then click Next .
- If the wizard prompts you to install any other role services that are required by Identity Management for UNIX components, click Yes .
- After verifying your selections on the Confirm Installation Selections page, click Install .The computer must be restarted after the installation of Identity Management for UNIX finishes.
In Server 2012 do the following:
Right-click Windows PowerShell and click Run as Administrator. Run each of the following commands:
- Dism.exe /online /enable-feature /featurename:adminui /all to install the administration tools for Identity Management for UNIX.
- Dism.exe /online /enable-feature /featurename:nis /all to install Server for NIS
- Dism.exe /online /enable-feature /featurename:psync /all to install Password Synchronization
A restart of the computer is required when you install Identity Management for UNIX.
Once you’ve done that, we’ll need to do some additional configuration. Open up Active Directory Users and Computers. Make a standard group for your *nix administrators. Then right-click the group and choose the UNIX Attributes tab:

Additionally, you’ll need to edit the properties of any user you plan on giving access to a *nix box. Open up Active Directory Users and Computers and right-click a user account, then select the UNIX Attributes tab:
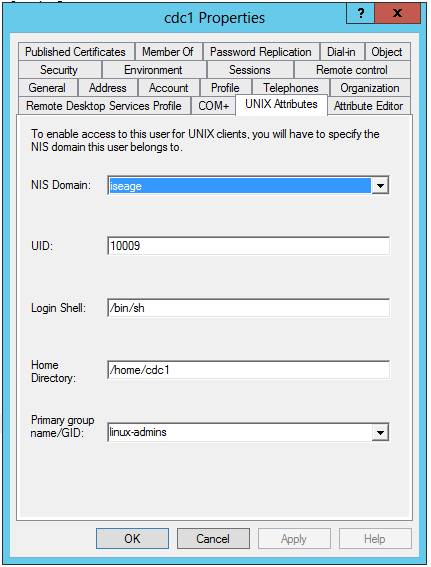
Use the primary group you made earlier.
One last thing: You’ll need to make a standard user in Active Directory for your *nix systems to bind with in order to perform LDAP queries. This user doesn’t have to have any special permissions but it’s a good idea to check the “user can never change password” box when creating it.